Managing Password Policies
A password policy is a set of requirements or rules, such as the number of characters required for a password. To enforce security during logins, policies are applied to scripts.
The policy ensures that the values of the variables comply with specified rules governing their composition. Although this feature is called password policies, these policies can be used on any variables, not just password variables.
You can set password policies for the following:
- A container or OU
- A User object
- An individual application
SecureLogin can generate random passwords. (See "ChangePassword" in the Nsure SecureLogin 3.51.2 Scripting Guide.) These passwords comply with password policies and significantly increase security. Typically, password rules are matched to the organizational policy for the application. However, SecureLogin can enforce stronger policies if they are required.
You can set a different password policy for each container or OU in the directory.
Creating or Editing a Password Policy
-
Click Password Policies.
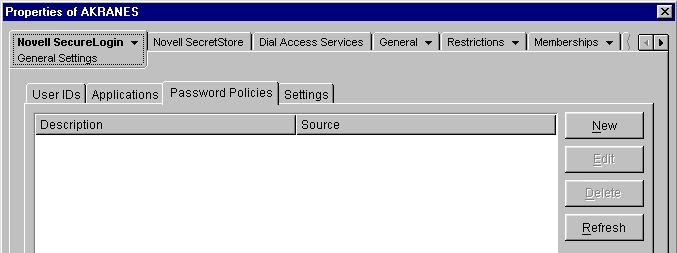
The Description column displays the name of the password policy. A down-arrow
 on the icon indicates that the policy is inherited.
on the icon indicates that the policy is inherited.The Source column displays the distinguished name of the object that contains the password policy (the container that the policy is inherited from).
SecureLogin enforces only new or more restrictive edited policies when a password is created or changed. SecureLogin doesn't check existing passwords to see whether they conform to new or edited policies.
-
Click New, enter a descriptive name for the new policy, then click OK.
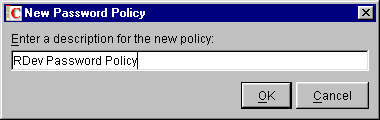
Use a unique name for all password policies, user IDs, and applications. A password policy can't have the same name as any other SecureLogin object.
-
(Conditional) If you are editing a policy, click the policy name, then click Edit.
-
Edit the settings, then click OK.
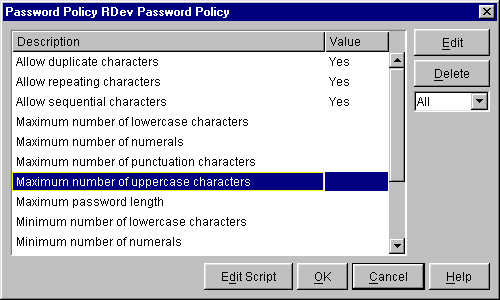
By default, several basic settings are displayed. To display all settings (basic and advanced), select All from the drop-down list below the Delete button.
You can edit more than one setting before clicking OK.
Not all settings are mandatory. You can set as few or as many policy restrictions as are necessary to meet security requirements.
To modify a setting, select it, click Edit, then type or select a value in the Value edit box.
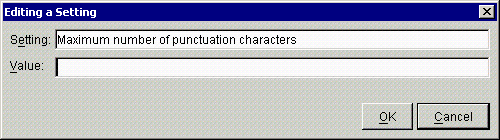
If you change a value for a setting, the new value appears in the Value column and in the modified script for the password policy. To see the changes to the script, click Edit Script.
For example, if you set the value of Maximum Number of Numeric Characters to 3, the script (available through Edit Script) displays MAXNUMERALS 3.
By default, the settings are case sensitive. For example, "a" is a different character from "A." Even if repeating characters aren't allowed, the password AaBC is still accepted.
The following table lists default values for basic settings:
The following table lists default values for advanced settings:
Setting Value Details Allow duplicate characters
Yes/No
No, case insensitive
The No option doesn't prohibit uppercase or lowercase use of the same character.
ABCA contains a duplicate character, but ABCD doesn't.
Allow repeating characters
Yes/No
No, case insensitive
The No option isn't case sensitive. Therefore, it doesn't prohibit uppercase or lowercase of the same character.
AABC contains a repeating character, but ABCA doesn't.
Allow sequential characters
Yes/No
No, case insensitive
The No option isn't case sensitive.
ABCD and 1234 contain sequential characters, as do BDAC and 4321.
Maximum number of lowercase characters
whole number
minimum zero, no upper limit
Maximum number of numerals
whole number
minimum zero, no upper limit
Maximum number of punctuation characters
whole number
minimum zero, no upper limit
Minimum number of lowercase characters
whole number
minimum zero, no upper limit
Minimum number of numerals
whole number
minimum zero, no upper limit
Minimum number of punctuation characters
whole number
minimum zero, no upper limit. See Allowable Punctuation Characters.
Password must not contain any of these characters
keyboard characters
case sensitive
If you set a minimum and maximum option to the same number, the password contains that number of letters. If the minimum number is higher than the maximum number, you receive an error.
Changes are saved to the script for the policy. To view changes you have made to the script, click Edit Script. Later, you can easily edit these changes by again using the Edit Script feature.
-
Save the settings by clicking Apply.
Allowable Punctuation Characters
The following characters satisfy the punctuation setting:
Using Password Policies in Scripts
Within a script, you can use a password policy to restrict a variable to the assigned security settings.
-
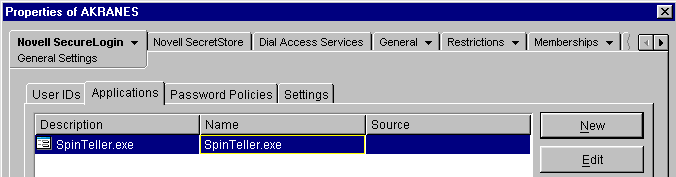
Click Applications.
-
Click the required application, then click Edit.
-
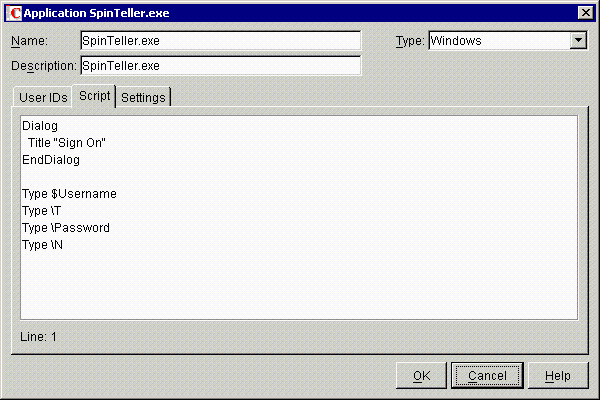
Add the following line to the top of the script:
RestrictVariable variable name password policy
For example, for SpinTeller.exe shown in Step 2, add
RestrictVariable $Password PasswordPolicy2
To restrict multiple variables to a particular password policy, add multiple RestrictVariable commands.
The variable name parameter can be a normal variable (for example, $Password), or a runtime variable (for example, ?temp). This flexibility can be useful if you change a password by using a runtime variable and then set a normal variable to the value of the runtime variable.
Adding the RestrictVariable command ensures that a variable complies with the policy. The value entered is rejected if it doesn't comply with the policy set for that variable. The RestrictVariable command applies the policy specified regardless of whether the variable is being added or edited through SecureLogin administration tools or through a script that is running.
If the value being changed by a user is not accepted, a message informs the user as to why the value was rejected.
If the value is being set through the ChangePassword command being run in automatic (random) mode, the value generated will comply with the policy.
In some cases, a policy might be created where no acceptable values exist. When this occurs, an error is displayed when the ChangePassword command tries to generate a password.
If you use the SecureLogin SET command to set values, they will not be forced to comply with password policies.
For more information, see "RestrictVariable" in the Nsure SecureLogin 3.51.2 Scripting Guide.
Example Password Policy Scripts
Example 1
MAXPASSWORDLENGTH 8
MINPASSWORDLENGTH 8
MAXPUNCTUATION 0
MINPUNCTUATION 0
MAXUPPERCASE 8
MINUPPERCASE 0
MAXLOWERCASE 8
MINLOWERCASE 0
MAXNUMERALS 8
MINNUMERALS 0
This password policy indicates that the password must be exactly 8 characters long and contain no punctuation characters.
The password asdf4jB8 is acceptable.
The password aasdf5$n is unacceptable because it contains a punctuation character.
Example 2
MAXPASSWORDLENGTH 12
MINPASSWORDLENGTH 6
MAXPUNCTUATION 8
MINPUNCTUATION 0
MAXUPPERCASE 8
MINUPPERCASE 0
MAXLOWERCASE 8
MINLOWERCASE 0
MAXNUMERALS 8
MINNUMERALS 0
NODUPLICATECHARACTERS CASEINSENSITIVE
POSITIONCHARACTER NUMERAL 3,4,5
This password policy indicates that the password must be between 6 and 12 characters long. It can contain no more than 8 of any character type (uppercase, lowercase, numeral, or punctuation). No character can appear more than once in the policy, regardless of case. A numeral must appear in at least one of positions 3, 4, or 5.
The password f54v9)_Q is acceptable.
The password f5v)_QF7 is unacceptable because it has no numeral in positions 3, 4 or 5, and the letter F occurs in positions 1 and 7.
Example 3
MAXPASSWORDLENGTH 16
MINPASSWORDLENGTH 6
MAXPUNCTUATION 8
MINPUNCTUATION 0
MAXUPPERCASE 16
MINUPPERCASE 1
MAXLOWERCASE 16
MINLOWERCASE 0
MAXNUMERALS 16
MINNUMERALS 0
BEGINWITHUPPERCASE
DISALLOWEDCHARACTERS @&
This password policy indicates that the password must be between 6 and 16 characters long. It must contain at least one uppercase character. It can contain no more than 8 punctuation characters. It must begin with an uppercase character, and it can't contain either the @ character or the & character.
The password R48iv"? is acceptable.
The password R48?- is unacceptable because it is less than 6 characters long.
Distributing Password Policies
You can configure password policies at the container, OU, or User object level. Policies set at the container or OU level apply to all associated User objects or user accounts. Policies set at the User object or user account level override all higher-level policies.
For ease of maintenance in multiple-user environments, we recommend that you maintain password policies at the container or OU level.
Setting the Default Domain Policy in Active Directory
In Active Directory environments, at the domain level, make sure that the Default Domain policy allows all authenticated users to have Read rights to All Properties.
-
Expand Active Directory Users and Computers, right-click the domain name, then click Properties.
-
Click Group Policy > Properties, then click Security.
-
Click Advanced.
-
Click Authenticated Users Special, then click View/Edit.
-
Under the Allow column, check the Read All Properties check box, then click OK.