Foreword
This document aims to give an overview of the ZENworks Mobile Workspace solution to IT department wishing to deploy within theirs premises. It gives the minimal configuration and hardware requirements needed for a proof of concept and the backend systems to which ZENworks Mobile Workspace can connect.
If the IT department wishes to proceed to a proof of concept using a production configuration, additional steps may be required (such as Kerberos authentication).
Overview
The following integration diagram represents a standard deployment of ZENworks Mobile Workspace with a public internet access through a company entry point. However, a proof of concept can be conducted without internet connection by using internal WiFi connection.
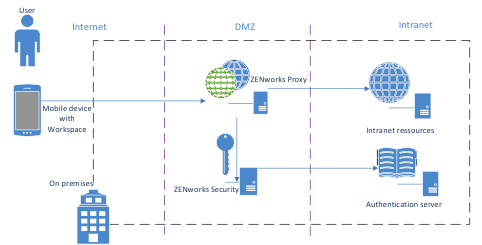
-
User: The user accesses his professional resources within the company’s infrastructure from his Smartphone (running iOS or Android).
-
ZENWorks Mobile / Smartphone: the Smartphone contains the ZENworks Mobile Workspace mobile application and is used to access company data through an internet/WiFi connection.
-
ZENWorks Security: The ZENworks Mobile Workspace security server is installed in the customer’s infrastructure and enables a centralized administration of the entire ZENworks Mobile Workspace solution.
-
ZENWorks Proxy: The ZENworks Mobile Workspace Proxy server allowing devices to access backend resources and Security server.
-
Authentication server: The Active Directory / LDAP Server is a pre-installed component in the Client’s infrastructure which enables the management and the authentication of the users.
-
Backend resources: Backend resources, such as Microsoft Exchange or IBM Lotus domino, SharePoint or OpenFire is a pre-installed component in the infrastructure which contains users’ sensitive data.
hosting machine
ZENworks Mobile Workspace solution is shipped as a multi-platform installer that can be executed on Linux or Window operating system. In both cases, a graphics and console mode is available.
Installing ZENworks Mobile Workspace on Linux
The computer specifications to host a Linux server are the following:
-
Type: virtual or physical
-
Recommended resources:
-
2000 users: 2 x 2.2 GHz, RAM 4GB, HDD 30GB
-
5000 users: 4 x 2.2 GHz, RAM 8GB, HDD 50GB
-
-
Linux version: (systemd adoption)
Installing ZENworks Mobile Workspace on Windows
The computer specifications to host Windows server are the following:
-
Type: Virtual or physical
-
Recommended resources:
-
2000 users: 2 x 2.4 GHz, RAM 8GB, HDD 50GB
-
5000 users: 4 x 2.4 GHz, RAM 12GB, HDD 70GB
-
-
Minimum Windows version: Windows server 2008 R2 x64
Hosing environment check list

Network configuration
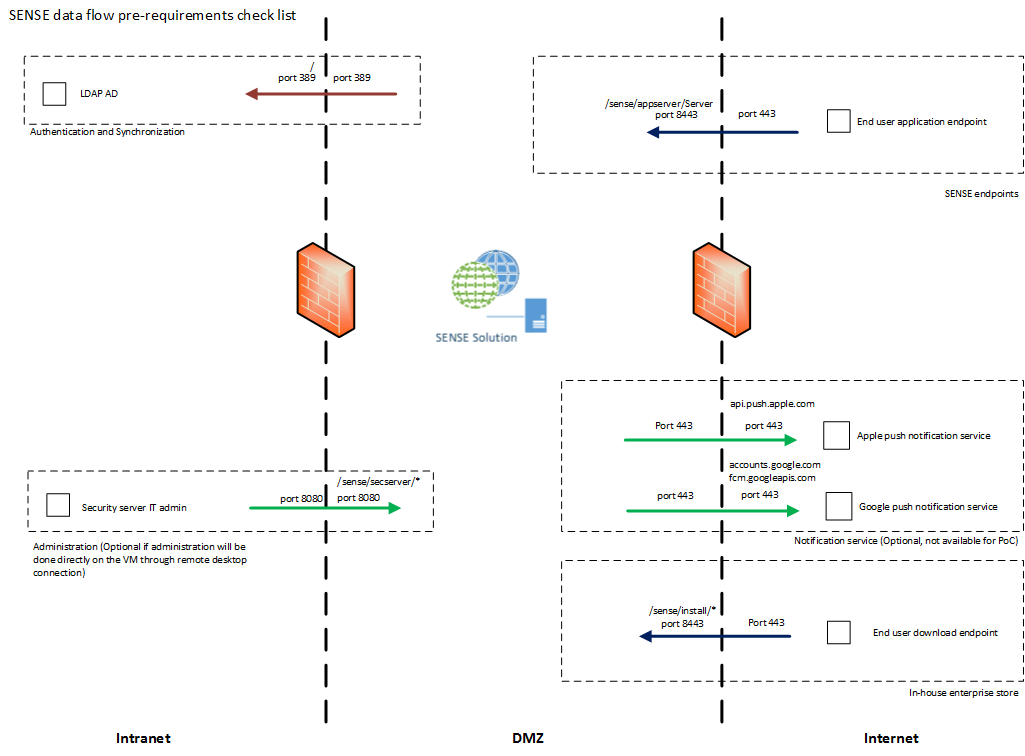
This part is linked to the data flow check list that can be helpful to follow the setup of the following steps.
LDAP
The ZENworks Mobile Workspace Server can synchronize user groups with the company’s LDAP directory. To achieve this, ZENworks Mobile Workspace will connect to LDAP server and retrieve groups and users. Therefore, it is necessary to create a bind user (read only) to allow ZENworks Mobile Workspace to browse the LDAP directory.
Synchronization
ZENworks Mobile Workspace native LDAP connector is seeking for LDAP groups belonging to the following object class: group, groupOfNames, groupOfUniqueNames, posixGroup. When finding such a group, it must have at least one of the following fields set: uid, givenName, sn, distinguishedName. LDAP which does not match these criteria will be ignored.
When a group is selected, ZENworks Mobile Workspace will list all users belonging to that group according to the field uniqueMember or member of each user. If not defined (cf. security server manual), the default attribute used as username is the field sAMAccountName for Active Directory server and cn for other LDAP implementations. If available, the given name (field givenName) and the surname (field sn) are retrieved and displayed in the administration Web console (Helpful if the username is anonymous).
Authentication
ZENworks Mobile Workspace has the ability to authenticate an user on any LDAP attribute chosen as username for the synchronization. To do so, a research is done to retrieve the user distinguishedName (DN) before any authentication attempt. Therefore, the authentication process is done based on the user DN and his password.
If the authentication has succeeded, the user’s session is enriched with the following LDAP attributes defined for that user: cn, displayname,description, dn, uid, sAMAccountName, userPrincipalName, mail, sn, givenName, distinguishedName. Therefore, it will be possible to choose one of those fields as the parameter (username) needed for backend authentication. A LDAP username used for authentication may not be usable to be used for authentication of the user against a backend server such as Exchange, SharePoint or WEB application.
However, if backend resources such as mail server (Exchange, Domino), content management system (SharePoint) or web resources need authentication, the password used to log into ZENworks Mobile Workspace must be the same as the one used for the target resources (SSO). This is usually the case for most of standard AD/Exchange/SharePoint installations.
Enabling password change capability
ZENworks Mobile Workspace provides the capability to allow users changing their password from the mobile devices even when the password has already expired. This feature requires to use LDAP over SSL (LDAPS) protocol.
|
Known issue : Too many grace logins are consumed when trying to connect the LDAP and change an expired password. User’s account could be blocked if the number of grace logins allowed is low. This issue affects eDirectory and standard LDAP servers (does not affect Active Directory). Workaround : Increase the number of grace logins allowed by multiplying the current value by 3 for eDirectory and 5 for standard LDAP system. |
Firewall
ZENworks Mobile Workspace servers are listening by default on port 8080 and 8443 for incoming HTTP(S) requests.
Firstly, please ensure that these ports are not blocked by the host operating system’s firewall. If an external firewall is used in front of ZENworks Mobile Workspace, port translation rules can be defined like the following one:
-
Internet → 80 translated to 8080 → ZENworks Mobile Workspace (can be even blocked to avoid connection without SSL)
-
Internet → 443 translated to 8443 → ZENworks Mobile Workspace
It is not mandatory to translate ports but it is better to use standard HTTP ports to avoid problems with other systems/ISPs blocking nonstandard port.
Reverse Proxy
Even if ZENworks Mobile Workspace ACL can prevent unauthorized access to administration console, a reverse proxy is recommended to avoid any direct access from Internet to ZENworks Mobile Workspace server. To allow access to required parts of ZENworks Mobile Workspace system, the following white list entries can be defined on proxy:
-
User authentication, authorization and application access: It will be used to allow access to backend system such as mail server, CMS and web application. The rule for this entry point is /sense/appserver/Server.
-
Enterprise store: It will be used by end users to authenticate themselves in order to get their enrollment code and download the application for the first time. The rule for this entry point is /sense/install/*.
Reverse proxy may also be used to filter ZENworks Mobile Workspace request based on User-Agent. This may prevent any automatized attack to reach the ZENworks Mobile Workspace server.
ZENworks Mobile Workspace administration
ZENworks Mobile Workspace administration is available through a standard Web Browser (Minimum requirement: Google Chrome, Firefox and Safari. Some refreshing issue may happen with Internet Explorer but IE8 gives good results):
-
/sense/secserver : Administration of ZENworks Mobile Workspace security server:
-
Manage domains and domain admin as super admin
-
Manage security policies
-
Manage devices, users and groups
-
Manage ZENworks Mobile Workspace applications
-
Manage access rights
-
Manage mail server settings
-
Manage CMS server settings
-
For administration comfort, this console can be available from intranet to avoid remote desktop connection to access the administration Web console. Therefore, administrators can manage the solution from their preferred web browser.
TLS
Trusted TLS connection is mandatory for downloading and updating any application since iOS 7.1 (list of trusted CA). Before production, the customer will be responsible to get a signed certificate from trusted CA. During a PoC, three options are available to conduct the test:
-
The application can be installed manually using Apple Configuration Utility for Windows (no more supported by Apple) or Apple Configurator 2 for Mac.
-
Use an internal CA to sign your servers certificates according to these instructions. And install the CA’s certificate on each iOS device as described here.
-
Use Sysmosoft HTTP proxy which will provide a trusted certificate and redirect the request to your server.
Network configuration check list
Mobile devices
iOS devices
All iOS devices are compatible with ZENworks Mobile Workspace as long as they are running iOS starting version 10.0 or higher. Dedicated views are available for tablet format.
| Jailbroken devices are not allowed. |
ZENworks Mobile Workspace application can be only deployed through enterprise store. There is no available version on public AppStore. Therefore, enterprise iOS applications must be signed with an Apple Enterprise Certificate. For PoC, Sysmosoft will use its own certificate but it is mandatory to have your own to go in production. To have your own certificate, you can apply here https://developer.apple.com/programs/ios/enterprise/ or ask Sysmosoft to do it for you. The full process can takes up to 2 weeks.
Android devices
ZENworks Mobile Workspace is compatible on Android devices running from version 4.4 (Kit Kat).
| Rooted devices are not allowed. |
Sysmosoft does not support issues caused exclusively by an operating system customization (e.g manufacturer operating system layer).
ZENworks Mobile Workspace has been tested specifically on the following devices and operating systems :
-
LG Nexus 4 (operating system 5.0.1)
-
LG Nexus 5 (operating system 6.0.1)
-
LG Nexus 5X (operating system 7.1.2)
-
Samsung Galaxy S4 mini (operating system 4.4.2)
-
Samsung Galaxy S4 (operating system 5.0.1)
-
Samsung Galaxy S6 (operating system 6.0.1)
-
Samsung Galaxy S7 (operating system 6.0.1)
-
Motorola Nexus 6 (operating system 6.0)
-
Huawei Nexus 6P (operating system 7.1.1)
-
Asus Nexus 7 (operating system 5.0.2)
-
HTC One (operating system 5.0.1)
Backend data sources
MS Exchange mail server
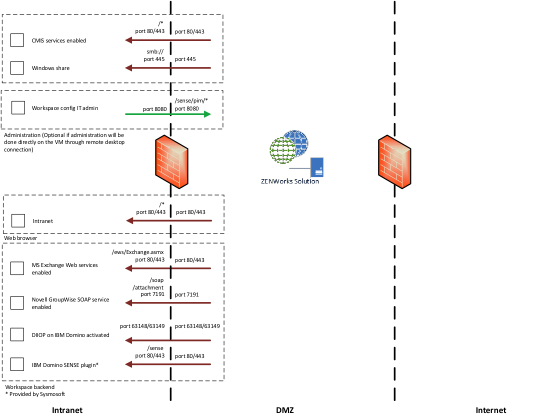
ZENworks Mobile Workspace can connect to MS Exchange 2007, 2010, 2013, 2016 and Office365 through Exchange Web Services (EWS: http://msdn.microsoft.com/en-us/library/office/dd877012.aspx). This requires EWS to be enabled. To verify if EWS are enabled, go to the page http(s)://<exchange_host_name>/ews/Services.wsdl. You should be prompted for username and password. If credentials are correct, a WSDL file should be displayed.
BASIC, DIGEST and NTLM authentication are supported and ZENworks Mobile Workspace can be set to avoid NTLM if required. When using Exchange, the authentication is usually done on Active Directory.
IBM Lotus Domino server
ZENworks Mobile Workspace can connect to IBM Lotus Domino starting version 8.5 through Domino IIOP connection (DIIOP: http://www-10.lotus.com/ldd/dominowiki.nsf/dx/DIIOP_Usage_and_Troubleshooting_Guide). This requires DIIOP services to be enabled.
Domino connector is based on IBM remote client library (NCSO) which is incomplete. To be able to access all required features, a ZENworks Mobile Workspace Domino plugin (Domino servlet) must be deployed on the server. This requires Domino HTTP server to be enabled.
When using Domino, the authentication will be done on Domino LDAP server with username and Domino internet password.
Enable TLS connection between ZENworks Mobile Workspace and IBM Domino
This section aims to describes how to setup ZENworks Mobile Workspace to enable TLS connection and how to add the Domino certificate to be trusted by ZENworks Mobile Workspace.
Enable TLS on ZENworks Mobile Workspace
-
Using a WEB browser, go to the security administration console. (/sense/secserver).
-
Log in as superadmin.
-
Edit the wanted domain under DOMAINS.
-
Click on the PIM tab.
-
Check the checkbox "Connect using SSL?".
Create a key ring on Domino
Open the Server Certificate Admin (certsrv.nsf) database on a Domino server and use its forms to create and populate a key ring. See Administering the Domino System, Volume 2 or the Domino Administrator Help for detailed information. For testing purposes, you can use the CertAdminCreateKeyringWithSelfCert form to create a key ring with a self-certified certificate.
Move the keyring to the server
The keyring consists of a keyring file (KYR file) and stash file (STH file). These files are generated on the computer from which you’re accessing the Server Certificate Admin database. Move or copy the two keyring files to the computer containing the Domino server. Place them in the server’s data directory. For example, if you create a keyring with a self-certified certificate using default names and copy the files to a computer with a server whose data files are installed at C:\Lotus\Domino\Data, the server files would be:
C:\Lotus\Domino\Data\selfcert.kyr C:\Lotus\Domino\Data\selfcert.sth
Enable SSL on Domino
In the Server document in the server’s Domino Directory, go to the Ports tab, then the Internet Ports tab. Under SSL settings, specify the SSL key file name (for example, selfcert.kyr). Go to the DIIOP tab. Ensure that the SSL port number is correct-it defaults to 63149. Enable the SSL port. Set Name & password and Anonymous authentication as desired.
Install the certificate on ZENworks Mobile Workspace
Once the keyring files are on the server, starting or restarting the DIIOP task generates a file named TrustedCerts.class in the Domino data directory. Copy that file to $ZENworksMobileWorkspace_HOME/lib.
Steps 3.2 to 3.4 has been copied form the following site: http://blueteetech.wordpress.com/2007/08/02/configure-ssl-on-domino/
Restart the ZENworks Mobile Workspace server
Novell Groupwise
ZENworks Mobile Workspace can connect to Novel Groupwise 2014 R2 through SOAP Web Services (https://www.novell.com/developer/ndk/groupwise/groupwise_web_service_(soap).html). This requires SOAP services to be enabled. To verify if SOAP are enabled, go to the page http(s)://<groupwise_host_name>:7191/soap. You should see a HTTP 200 response page.
CMS server
CMIS server
ZENworks Mobile Workspace can connect to SharePoint 2010 , 2013, 2016 and any CMIS compatible CMS. For SharePoint, connection is done through CMIS connector (SP 2013: http://msdn.microsoft.com/en-us/library/office/jj945829.aspx, SP 2010: technet.microsoft.com/en-us/library/ff934619.aspx). This required CMIS connector to be activated with Basic or NTLM authentication enabled.
When using SharePoint, the authentication is usually done on Active Directory.
Windows share folder
ZENworks Mobile Workspace can connect to any share folder through the SMB protocol. Access rights will be the same as those defined in the Active Directory.
Internal WEB applications
ZENworks Mobile Workspace secure browser uses ZENworks Mobile Workspace standard HTTP proxy to allow users to browse enterprise intranet. This involves opening routes from ZENworks Mobile Workspace server to such web application.
ZENworks Mobile Workspace Proxy will try to do SSO on web application using HTTP authentication of type: basic, digest, ntlm, and Kerberos. To be able to use SSO, web application must have the same login credentials as the LDAP credentials. Otherwise, the application may display a login page to prompt the user to enter specific username and password.
Most of Web applications have not been designed for mobile devices with small screen and bad network connection. Dedicated entry point and pages may enhance user experience.
Workspace network configuration check list
Updating the keystore (Only if ZENworks Mobile Workspace is not behind a reverse proxy or FW)
Even if ZENworks Mobile Workspace server has been installed without SSL connection, a SSL interface has been configured anyway with an auto generated self-signed certificate. To enable SSL with a trsuted certificate, we only need to replace it.
-
Start the application portecle provided with ZENworks Mobile Workspace installer package (./tools/portecle-launcher.bat)
-
Open the keystore file ($ZENworksMobileWorkspace_HOME/conf/keystore.jks)
-
Enter the auto generated password at installation. It can be found in the file $ZENworksMobileWorkspace_HOME/conf/server.xml in the attribute keystorePass of the SSL Connector.
-
Remove the auto generate certificate
-
Import the trusted key pair (Tools → Import Key Pair)
-
Enter the password of the key pair
-
Save the keystore